RedAlert, also known as N13V, is a new ransomware operation that encrypts both Windows and Linux VMWare ESXi servers in attacks on corporate networks.
The crime of yesterday’s magnitude was discovered by MalwareHunterTeam today. The team published screenshots highlighting where the leak occurred.
The ransomware has been branded as ‘#RedAlert’ upon being obtained by means of a ransom message from a webpage known as B2false. However, from a password-unlocking device procured by BleepingComputer, the ransomware’s developers have created the name ‘N13V’ internally, as shown next.

The Linux encryptor was created to target VMware ESXi servers, with command line options that allow the threat actors to stop running virtual machines so as to disable discrete virtual machines before locking away data. New RedAlert Ransomware targets Windows, Linux VMware ESXi servers.
The full set of command-line parameters can be seen below for New RedAlert Ransomware targets Windows, Linux VMware ESXi servers.
- w Runs the halt command for stopping all running virtual machine files
- p Path to encryption (by default encrypt files and directories in scope, but not include any subdirectories)
- f File for encryption
- r Recursive. used when typing a duty and path with p (search and encryption will include subdirectories)
- t Checks time for encryption (only encryption, without key-gen, memory allocates …)
- n Not mounted to browse encrypted folders. (Show files and folders with some info)
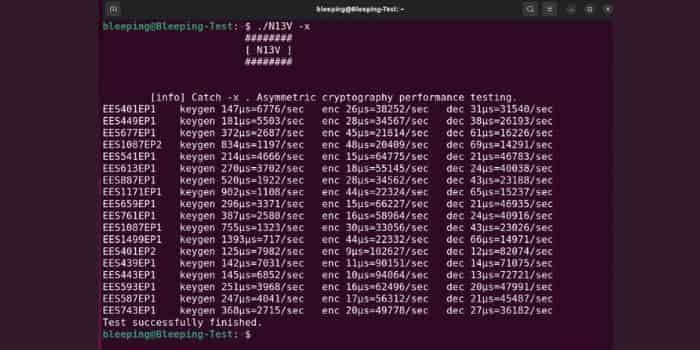
- x Asymmetric cryptography performance tests. DEBUG TESTS
- h Show this message.
When running the ‘-w’ argument of the ransomware, the Linux encryptor shuts down all running VMware ESXi virtual machines with the esxcli command.
esxcli –formatter CSV –format-param fields “WorldID,DisplayName” vm process list tail -n 2 awk -F “‘,'” system(“esxcli vm process kill –type force –world-id ” $1) “
The ransomware uses the NTRUEncrypt public-key encryption algorithm to secure various “Parameter Sets” that offer different levels of security.
Particularly interested users of RedAlert N13V will appreciate the actuator option ‘-x’ from the command line, which performs ‘crypto asymmetric performance testing’ with various parameters. At the moment, however, it cannot be made clear whether it is possible to force a particular parameter set when encrypts, or if it will choose a more effective one.
Among all ransomware programs known to use this particular encryption code, only FiveHands utilizes it.
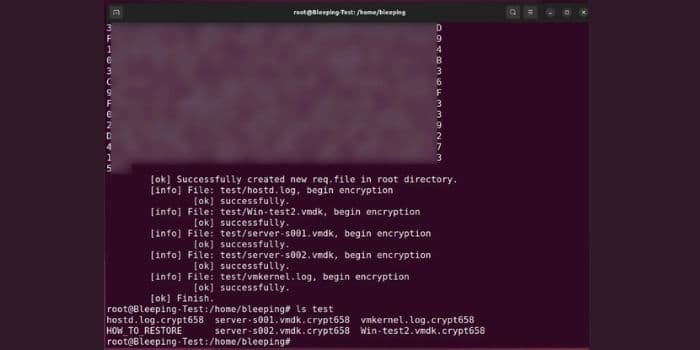
When encrypting files, ransomware will only target VMware ESXi virtual machine files, such as log files, swap files, virtual disks, and memory files, as can be listed below.
In the analyzed sample by BleepingComputer, the ransomware encrypted these file types using the XOR algorithm and appended the letter “.crypt” to the file name of the encrypted files.

In each folder, ransomware also creates a custom ransom note named HOW to restore, which contains information about the missing information and a call reference to a unique TOR ransomware payment site for the sufferer.
The site related to the Tor payment service employs comparable methods to ransomware sites, as it demonstrates the ransomed demand and provides a place to negotiate with the threat actors.
RedAlert N13V only accepts Monero, the privacy coin, for payments. Although the Monero currency is often sold in digital-currency exchanges in the US, it is unavailable to most exchanges there.
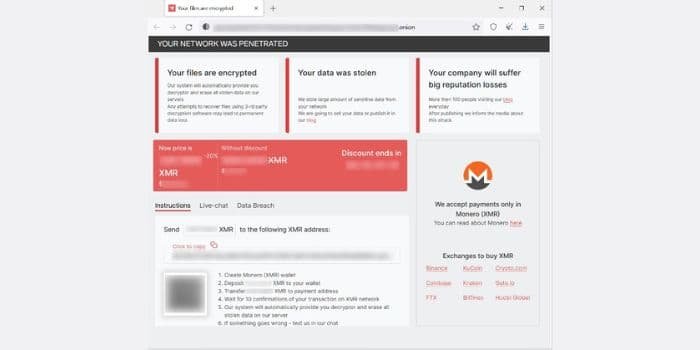
Although only a Linux encryptor has been discovered, the payment web page has significant indications showing that Windows decryptors can also exist.
“Shame Board”
Like nearly all brand-new financial ransomware attacks, RedAlert implements double-extortion hack attempts, which is when information is distorted, and then ransomware is manufactured to confine devices.
This tactic allows the extortionist to threaten blackmail by demanding ransom for money to unlock the device and prevent further distribution of the stolen data.
If a New RedAlert Ransomware targets Windows, Linux VMware ESXi servers demand is not met, the RedAlert gang publishes stolen data on their data leak website under a Creative Commons license so people can download it.
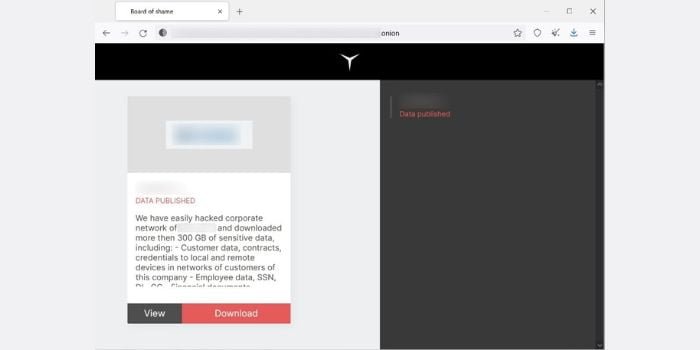
For the time being, the RedAlertTM website only contains data from one particular organization. This indicates that the site is relatively new.
The spread of this recently developed New RedAlert Ransomware targets Windows, Linux VMware ESXi servers attack proves that our team will have to be watchful regarding it, given its highly advanced features and rapid recognition of at least one of the two OS platforms.